
My SOURCE Seattle presentation on a Heart of Darkness style journey through startups, carriers, DDoS, and record setting disruptions by people who implicitly admit to their actions and somehow avoid consequences.



Introduced to some edgy teens who had a 500k/yr basement op doing BGP anycast style ddos mitigation (or rather, managing a reselling of one) beating out the biggest businesses where fixed costs were already carried by an existing client base.
Some founder friction but still seemed promising based on the lack of movement in carrier space since they didn’t want to solve these problems and seemed to have unlimited resources to throw at problems they don’t want to solve.
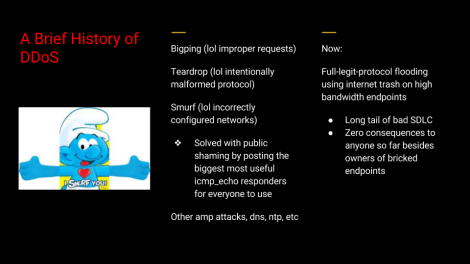
If you haven’t been around a while, DDoS has been a thing for a long time and many construct whole intellectually dishonest philosophies for why they should be allowed to wreck internet ecosystems. They always boil down to a baseless claim of why it’s justified to commit a huge pile of crimes and wreck carnage across whole geographies of infrastructure because “I want.”
Since these new attacks are employing fully stateful legitimate traffic and not amplification attacks or crafted attacks exploiting old busted junk in protocols themselves, but rather, new busted junk that has been irresponsibly shipped because there is no such thing as software liability and likely never will, this is now the new normal

Having a competitive advantage of access to c2 data certainly makes the job of defending against the attacks from that same c2 a lot easier.




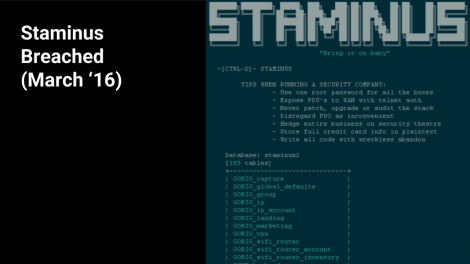
https://krebsonsecurity.com/2016/03/hackers-target-anti-ddos-firm-staminus/
https://www.riskbasedsecurity.com/2016/03/staminus-breach-just-how-bad-is-it/
“St4m|nu5″ root
https://pastebin.com/qV0rPNfP
https://gizmodo.com/hackers-broke-into-a-security-company-and-stole-the-kkk-1764343816

https://krebsonsecurity.com/2016/09/israeli-online-attack-service-vdos-earned-600000-in-two-years/
https://krebsonsecurity.com/2016/09/alleged-vdos-proprietors-arrested-in-israel/
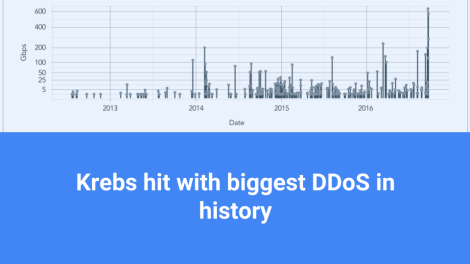
https://krebsonsecurity.com/2016/09/krebsonsecurity-hit-with-record-ddos/
https://krebsonsecurity.com/2016/10/spreading-the-ddos-disease-and-selling-the-cure/


http://seclists.org/nanog/2016/Sep/222
https://www.webhostingtalk.com/showthread.php?t=1598981
I would ask you to think about this image the next time you decide that using publicly routable addresses/interfaces for private/critical networks is totally fine.

Doug Madory – Dyn
NANOG 68 BackConnects Suspicious BGP Hijacks
https://krebsonsecurity.com/2016/09/israeli-online-attack-service-vdos-earned-600000-in-two-years/
https://krebsonsecurity.com/2016/09/ddos-mitigation-firm-has-history-of-hijacks/
https://dyn.com/blog/backconnects-suspicious-bgp-hijacks/
Reselling Voxility:
https://www.linkedin.com/company/voxility
https://www.voxility.com/anti-ddos
https://www.voxility.com/anti-ddos/Anti-DDoS+Tunnel+for+Networks
https://tools.ietf.org/html/bcp38
Click to access philip-smith-bgp-techniques.pdf

https://krebsonsecurity.com/2016/10/ddos-on-dyn-impacts-twitter-spotify-reddit/
https://dyn.com/blog/dyn-statement-on-10212016-ddos-attack/
Users reported sporadic problems reaching several websites, including Twitter, Netflix, Spotify, Airbnb, Reddit, Etsy, SoundCloud and The New York Times.
Think about what the ability to undetectably MitM partner networks does to third party compliance and network security controls.
Unless you have your own Dyn-like BGP global observatory collecting Tbyes per day from globally distributed sensors continually performing traceroutes and have somehow automated alerting to malicious changes worldwide, you basically won’t know if your internet links are being hijacked definitively.
Fallout from record-setting global IoT DDoS:
- No news
- No charges
- No convictions
- No real attention of any kind as yet even though various rich and powerful people were personally affected and global clouds/nets experienced significant downtime
Other possibilities:
Leveraging mitigated ASNs to attack others (or whoever) when not authorized for this purpose. The ability to differentiate a legit BGP announcement and an illegitimate one has not been something that peering has wanted to do. There are many reasons for this.
Conclusion: if your crime and tactics is very technical in nature, you can expect to be ignored indefinitely.
When Dyn was sold to Oracle a month later after losing ~14k client domains, what’s the measurable damage to those equity holders? Undisclosed buyout price was estimated at ~$600M
Oracle acquires DNS provider Dyn, subject of a massive DDoS attack in October
https://dyn.com/blog/dyn-statement-on-10212016-ddos-attack/

https://krebsonsecurity.com/2016/10/source-code-for-iot-botnet-mirai-released/
More than one million consumer web-connected video cameras and DVRs are compromised by bot herders who use the devices for DDoS attacks, researchers say.
uPNP being enabled by default in current year isn’t helping.
[[ Poll: does anyone here understand how BGP or other high level internet routing protocols work? What about peering relationships and how those interact with nation-state politics? ]]

Nothing is off the table in word or action:
- Slander and harassment in relationship management
- DDoS and botnet attacks as a sales strategy
- Business/wire fraud without awareness of exposure and consequences; all tainted equity and business value essentially worthless or worse
- Running business processes using rootshells on containers deployed on bulletproof hosting on hijacked IP space, managed via tor, and paid with btc
- No decent contracts or formalized relationships (and no awareness of why this is a bad thing)
- The list goes on
Intermixing of crime and business based on Dyn’s report of their activities and similar reporting:
- DDoS of prospective clients while in the RFP process to force sales
- Trolling the competition at 3am using fake documents and fake business identities instead of competitive market analysis
As per usual, hiring of employees and vendors focuses on the wrong things.
People are already tired of waiting for someone to address the ecosystem and have started destroying that low-hanging fruit creating, at long last, a market force of some kind. An imperfect one, but making internet hardware nonfunctional gets things done no matter the political hand-waving.
What happens when it’s no ones job to fix?
What if people responsible for these problems just let it go on for a decade(s) without any appreciable action? (because that is what has occurred)
Network effects of this broken bitrotting ecosystem:
- Brickerbots
- Vigilantism
- Wrecked businesses / firesale equity
- Bulletproof hosting
- Fronts for crime rings and subcontracted organized crime (highly optimized markets) that should be treated as a threat to national security/sovereignty
Current popular garbage-tier IoT destroying malware: Brickerbot / Wifatch / Hajime
BrickerBot is a vigilante worm that destroys insecure IoT devices
https://ics-cert.us-cert.gov/alerts/ICS-ALERT-17-102-01A
If you can buy the right to arbitrarily announce ASNs using fake identities and paying in crypto currency, really what can’t you do?

https://en.wikipedia.org/wiki/Realpolitik
https://en.wikipedia.org/wiki/Post-realism
https://en.wikipedia.org/wiki/Security_dilemma
No one should be in favor of any of this even if it serves their dishonest short-term goals because might-makes-right philosophies will always be used against you.

If you look through their actions, none of them solves these problems today or are they likely to start any time soon.
We all need to accept that no one is going to come and save us from poor architecture decisions and, with the possible exception of Oracle and Dyn, no one is going to buy us out.
https://www.terraform.io/intro/index.html
So if you can’t count on legit enterprise to fix problems and the upstarts have no integrity and will burn down your life for a dollar, what then?
- Infrastructure as code
- Contingency plans
- Automation of both
Doing nothing at all and having no viable plans whatsoever for business continuity and incident response isn’t a good idea unless your business doesn’t matter to anyone.
You can automate contingency plans for being attacked. You can leverage well defended and geospatially diverse global clouds. You can use private cloud options that are not internet routed like Azure’s government cloud stuff that has its own cross continental private fiber and is only accessible from internetwork exchange pops. It is, by design, immune from BGP hijacking and internet-based DDoS because it presents no threat surface from the internet.
Multinationals are building their own private internet because those running the present internet are not solving problems.
Deployment automation also has the nice side effect of having the age of infrastructure being hours or days old instead of maintaining unlimited amounts of bitrot and legacy exposures in production environments, the leading cause of breach and data exfiltration.
The status-quo of legacy trash becomes a colossal equity-destroying exposure of risk management and doing nothing as a plan becomes immediately and obviously untenable.
A couple followons from the last month:
https://www.wired.com/story/mirai-botnet-minecraft-scam-brought-down-the-internet/
https://krebsonsecurity.com/2017/12/mirai-iot-botnet-co-authors-plead-guilty/
http://archive.is/PQAnU